Hackers Target Gamers With Microsoft-Signed Rootkit
Por um escritor misterioso
Descrição
Kernel mode driver can download second-stage payload directly to memory, allowing threat actors to evade endpoint detection and response tools.
Sony, Rootkits and Digital Rights Management Gone Too Far
:max_bytes(150000):strip_icc()/GettyImages-1323900927-d4b8e26cf28f44129e189465fa5a73a8.jpg)
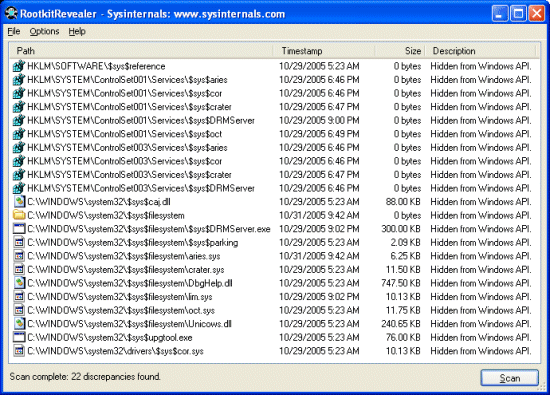
Rootkit Malware Found in Signed Windows Driver

Microsoft signed driver called Netfilter, turns out it contained
What is a Rootkit and How to Detect It - SOCRadar® Cyber

Retliften: How Microsoft Wound Up Certifying Malware - TeamWorx

The Hacker News on LinkedIn: Chinese Hackers Deploy Microsoft

The Hacker News on LinkedIn: Chinese Hackers Deploy Microsoft

How to detect & prevent rootkits

What is a Rootkit and How to Detect It? - Shiksha Online

Stealthy Universal Rootkit Let Attacker Load Payload Directly
Chinese Hackers Utilize Microsoft Signed Rootkit To Target The

Microsoft accidentally signed a gaming driver containing rootkit
Fire Chili Rootkit: Deep Panda APT Resurfaces With New Log4Shell

Chinese hacking group uses new 'Fire Chili' Windows rootkit
de
por adulto (o preço varia de acordo com o tamanho do grupo)